
Hello folks,Once again this is Ravi with a new topic “Quantum Cryptography”.First, what is cryptography ? Why do we need ?
Ever since mankind has existed, people have had secrets, and other people have wanted to know these secrets.Cryptography (from the Greek Krypto ‘hidden’ and Grafo ‘written’) is the study and implementation of techniques to hide information, or to protect it from being read.It tries to hide, encrypt, the information in such a way that a third party who has access to the hidden, encrypted, data cannot reconstruct, decrypt, the original information. So basically,
Cryptography is the art of devising codes and ciphers, and cryptanalysis is the art of breaking them. Cryptology is the combination of the two. In the literature of cryptology, information to be encrypted is known as plaintext, and the parameters of the encryption function that transforms are collectively called a key.
The earliest forms of cryptography were performed by pencil and paper, and of course were available only to those who had access to proper education. These classical ciphers were mainly transposition ciphers, which rearrange the letters in a message, and substitution ciphers, which replaced letters, groups of letters or words with other letters, groups or words. One of the earliest reported substitution ciphers was the Caesar cipher or Caesar’s shift, in which the letters of the alphabet were replaced by the letters of a second alphabet that was shifted a fixed number of positions again the normal alphabet. It was named after Julius Caesar who used it to communicate with his generals during his military campaigns.
Quantum cryptography is different from traditional cryptographic systems in that it relies more on physics, rather than mathematics, as a key aspect of its security model.It is based on the usage of individual particles/waves of light (photon) and their intrinsic quantum properties to develop an unbreakable cryptosystem – essentially because it is impossible to measure the quantum state of any system without disturbing that system. It is theoretically possible that other particles could be used, but photons offer all the necessary qualities needed, their behavior is comparatively well-understood, and they are the information carriers in optical fiber cables, the most promising medium for extremely high-bandwidth communications.

How it works :-

Let us assume that two people wish to exchange a message securely, traditionally named Alice and Bob.They try to keep a quantum-cryptographic key secret by transmitting it in the form of polarized photons,a scheme invented by Charles Bennett of IBM and Gilles Brassard of the University of Montreal during the 1980s and now implemented in a number of commercial products.
1. To begin creating a key,Alice sends a photon through either the 0 or 1 slot of the rectilinear or diagonal polarizing filters, while making record of the various orientations.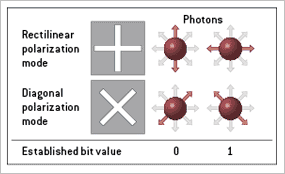
2. For each incoming bit, Bob chooses randomly which filter slot he uses for detection and writes down both the polarization and the bit value.
3.If eve the eavesdropper tries to spy on the train of photons,quantum mechanics prohibits her from using both filters to detect the orientation of a photon. If she chooses the wrong filter, she may creates errors by modifying their polarization.
4. After all the photons have reached Bob,he tells Alice over a public channels,perhaps by telephone or an email,the sequences of filters he used for the incoming photons, but not the bit value of photons.
5.Alice tells Bob during the same conversation which filters he chose correctly. Those instances constitute the bits that Alice and Bob will use to encrypt messages.
The main practical problem with secret-key encryption is determining a secret key. In theory any two users who wished to communicate could agree on a key in advance, but in practice for many users this would require secure storage and organization of a awkwardly large database of agreed-on keys.
If you enjoyed this Post, I’d be very grateful if you’d help it spread by emailing it to a friend, or sharing it on social network.Thank you ! keep hitting…
Interesting !! keep it up 🙂 awesome
if you get time try my new post . Thank you
I am sure you will like it !!
LikeLike
Thank you..!!
LikeLiked by 1 person